- TRANSDUCERS
- TRANSDUCERS
- BASIC COMPONENTS DK
- BASIC COMPONENTS DK
- MARKETPLACE
- MARKETPLACE
- DEVELOPMENT BOARDS & KITS
- DEVELOPMENT BOARDS & KITS
- CABLE ASSEMBLIES
- CABLE ASSEMBLIES
- RF AND WIRELESS
- RF AND WIRELESS
- BOXES ENCLOSURES RACKS
- BOXES ENCLOSURES RACKS
- AUDIO PRODUCTS
- AUDIO PRODUCTS
- FANS-BLOWERS-THERMAL MANAGEMENT
- FANS-BLOWERS-THERMAL MANAGEMENT
- WIRELESS MODULES
- WIRELESS MODULES
- TERMINALS
- TERMINALS
- Cables/Wires
- Cables/Wires
- SINGLE BOARD COMPUTER
- SINGLE BOARD COMPUTER
- BREAKOUT BOARDS
- BREAKOUT BOARDS
- LED
- LED
- TEST AND MEASUREMENT
- TEST AND MEASUREMENT
- POTENTIONMETERS AND VARIABLE RESISTORS
- POTENTIONMETERS AND VARIABLE RESISTORS
- DEVELOPMENT BOARDS AND IC's
- DEVELOPMENT BOARDS AND IC's
- EMBEDDED COMPUTERS
- EMBEDDED COMPUTERS
- OPTOELECTRONICS
- OPTOELECTRONICS
- INDUSTRAL AUTOMATION AND CONTROL
- INDUSTRAL AUTOMATION AND CONTROL
- COMPUTER EQUIPMENT
- COMPUTER EQUIPMENT
- CONNECTORS & INTERCONNECTS
- CONNECTORS & INTERCONNECTS
- MAKER/DIY EDUCATIONAL
- MAKER/DIY EDUCATIONAL
- TOOLS
- TOOLS
- MOTORS/ACTUATORS/SOLEENOIDS/DRIVERS
- MOTORS/ACTUATORS/SOLEENOIDS/DRIVERS
- FPGA HARDWARE
- FPGA HARDWARE
- ROBOTICS & AUTOMATION
- ROBOTICS & AUTOMATION
Description
Secure click carries the ATECC508A cryptographic coprocessor with secure hardware-based key storage. The click is designed to run on either 3.3V or 5V power supply. It communicates with the target microcontroller over I2C interface.
NOTE: The click comes with stacking headers which allow you to combine it with other clicks more easily by using just one mikroBUS™ socket.
ATECC508A features
Microchip's ATECC508A integrates ECDH (Elliptic Curve Diffie Hellman) security protocol, an ultra-secure method to provide key agreement for encryption/decryption. It also integrates the ECDSA (Elliptic Curve Digital Signature Algorithm) sign-verify authentication for the Internet of Things (IoT) market, including home automation, industrial networking, accessory and consumable authentication, medical, mobile and more.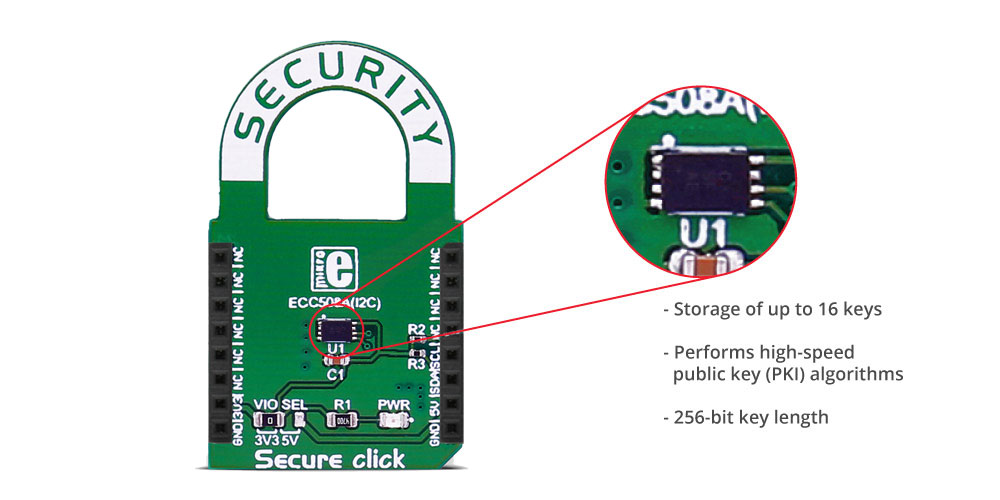
The ATECC508A includes an EEPROM array which can be used for storage of up to 16 keys, certificates, miscellaneous read/write, read-only or secret data, consumption logging, and security configurations. Access to the various sections of memory can be restricted in a variety of ways and then the configuration can be locked to prevent changes.
It features a wide array of defense mechanisms specifically designed to prevent physical attacks on the device itself, or logical attacks on the data transmitted between the device and the system. Hardware restrictions on the ways in which keys are used or generated provide further defense against certain styles of attack.
Specifications
| Type | EEPROM |
| Applications | IoT node security and ID, secure download and boot, ecosystem control, message security, anti-cloning, etc. |
| On-board modules | ATECC508A cryptographic co-processor |
| Key Features | Performs high-speed public key (PKI) algorithms, NIST Standard P256 elliptic curve support, SHA-256 hash algorithm with HMAC option, 256-bit key length, storage for up to 16 Keys |
| Interface | I2C |
| Input Voltage | 3.3V or 5V |
| Click board size | M (42.9 x 25.4 mm) |
- Home
- Secure click
Secure click
SIZE GUIDE
- Shipping in 10-12 Working days
- http://cdn.storehippo.com/s/59c9e4669bd3e7c70c5f5e6c/ms.products/5aa8c45961dd1b8f47f797d2/images/5aa8c45961dd1b8f47f797d3/5aa8c1d06e94773f6f5cb8cf/5aa8c1d06e94773f6f5cb8cf.jpg
Description of product
Description
Secure click carries the ATECC508A cryptographic coprocessor with secure hardware-based key storage. The click is designed to run on either 3.3V or 5V power supply. It communicates with the target microcontroller over I2C interface.
NOTE: The click comes with stacking headers which allow you to combine it with other clicks more easily by using just one mikroBUS™ socket.
ATECC508A features
Microchip's ATECC508A integrates ECDH (Elliptic Curve Diffie Hellman) security protocol, an ultra-secure method to provide key agreement for encryption/decryption. It also integrates the ECDSA (Elliptic Curve Digital Signature Algorithm) sign-verify authentication for the Internet of Things (IoT) market, including home automation, industrial networking, accessory and consumable authentication, medical, mobile and more.
The ATECC508A includes an EEPROM array which can be used for storage of up to 16 keys, certificates, miscellaneous read/write, read-only or secret data, consumption logging, and security configurations. Access to the various sections of memory can be restricted in a variety of ways and then the configuration can be locked to prevent changes.
It features a wide array of defense mechanisms specifically designed to prevent physical attacks on the device itself, or logical attacks on the data transmitted between the device and the system. Hardware restrictions on the ways in which keys are used or generated provide further defense against certain styles of attack.
Specifications
| Type | EEPROM |
| Applications | IoT node security and ID, secure download and boot, ecosystem control, message security, anti-cloning, etc. |
| On-board modules | ATECC508A cryptographic co-processor |
| Key Features | Performs high-speed public key (PKI) algorithms, NIST Standard P256 elliptic curve support, SHA-256 hash algorithm with HMAC option, 256-bit key length, storage for up to 16 Keys |
| Interface | I2C |
| Input Voltage | 3.3V or 5V |
| Click board size | M (42.9 x 25.4 mm) |
NEWSLETTER
Subscribe to get Email Updates!
Thanks for subscribe.
Your response has been recorded.
INFORMATION
ACCOUNT
ADDRESS
Tenet Technetronics# 2514/U, 7th 'A' Main Road, Opp. to BBMP Swimming Pool, Hampinagar, Vijayanagar 2nd Stage.
Bangalore
Karnataka - 560104
IN
Tenet Technetronics focuses on “Simplifying Technology for Life” and has been striving to deliver the same from the day of its inception since 2007. Founded by young set of graduates with guidance from ardent professionals and academicians the company focuses on delivering high quality products to its customers at the right cost considering the support and lifelong engagement with customers. “We don’t believe in a sell and forget model “and concentrate and building relationships with customers that accelerates, enhances as well as provides excellence in their next exciting project.


